Research
Next Generation Human Biometrics: Inconspicuity, Continuity, and Canceliability
-
† Inconspicuous Smartphone User Authentication
-
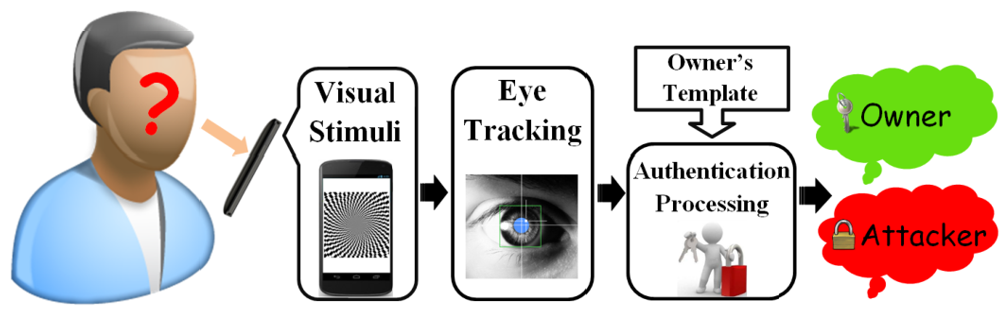
• Biometrics-based authentications on smartphones mostly fall into two folders: physiological and behavioral biometrics. The former one relys on the body components (e.g., fingerprint, face, iris). But they are exposed to the public and can be easily stolen and counterfeited. The latter one is based on the way people do things (gesture, keystroke, gait). However, it is still possible for the adversary to mimic via shoulder-sufing.
• My vision is to explore the non-intrusive, inconspicuous physio-behavioral biometric which naturally fuses two biometric modalities in such a complicated way that the credential is extremely difficult, if not entirely impossible, for the attacker to mimic or replicate. As the direct interaction method with the smartphone, human eye movement is driven by the complex network coordination between brainstem control and extraocular muscles, and therefore, contains diverse non-volitional human-dependent features. The successful exploration of eye-movement-based human credential can provide the smartphone users with an additional non-invasive security layer to reduce the vulnerability of the authentication process.
-
• Biometrics-based authentications on smartphones mostly fall into two folders: physiological and behavioral biometrics. The former one relys on the body components (e.g., fingerprint, face, iris). But they are exposed to the public and can be easily stolen and counterfeited. The latter one is based on the way people do things (gesture, keystroke, gait). However, it is still possible for the adversary to mimic via shoulder-sufing.
-
† Continuous Cardiac-based User Authentication System
-
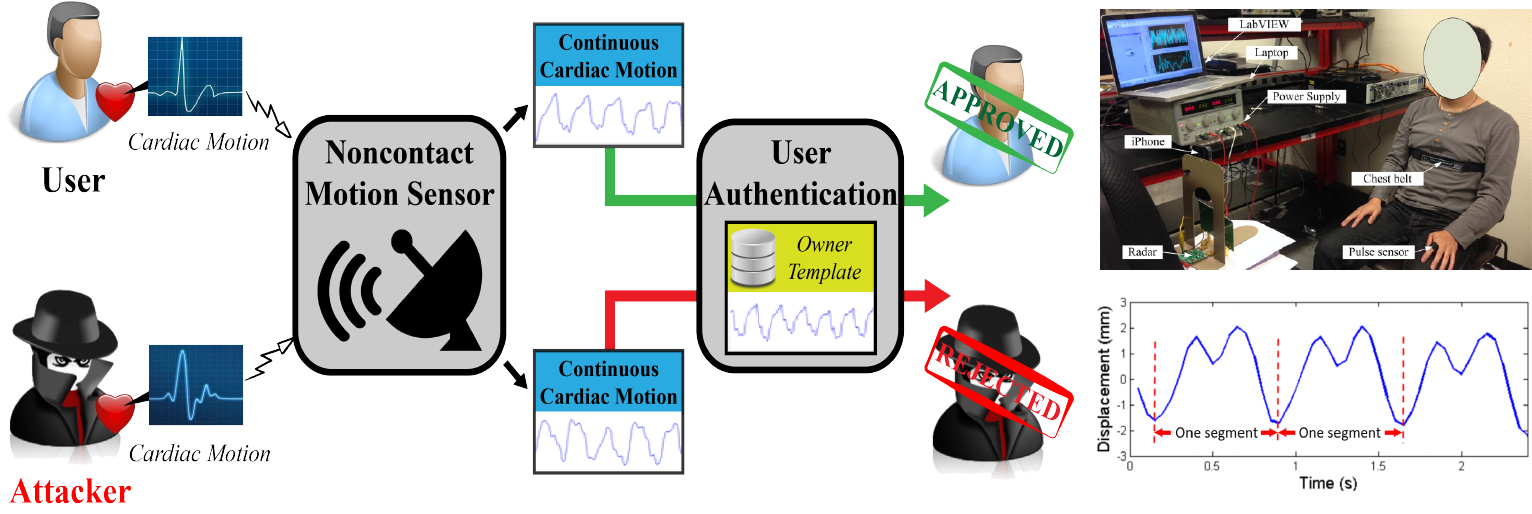
• Continuous authentication improves the vulnerable one-pass validation by continuously verifying the user&rsquto;s identity during session use, even long after the initial verification. Besides their security vulnerabilities, existing solutions periodically require the intentional engagement from the user, which harms the usability.
• As a live individual trait, heart-based biometric is unique (i.e., distinguishable across subjects), measurable (i.e., hard to hide), non-volitional (i.e., unknown to the user), secure (i.e., difficult to counterfeit), and present in all living individuals (i.e., intrinsic liveness). Different from electrocardiogram (ECG), we investigated the cardiac motion, a functional behavior determined by the intrinsic geometric structure of the heart.
• We developed Cardiac Scan, a secure and trustworthy continuous user authentication scheme via non-contact cardiac motion sensing. Specifically, the work includes building a smart DC-couple continuous-wave (CW) Doppler radar sensor to continuously capture the high-resolution cardiac motion information from the distance, and identifying fiducial descriptors of cardiac motion based on the heart geometric characteristics.
-
• Continuous authentication improves the vulnerable one-pass validation by continuously verifying the user&rsquto;s identity during session use, even long after the initial verification. Besides their security vulnerabilities, existing solutions periodically require the intentional engagement from the user, which harms the usability.
-
† Cancelable Brain Biometrics for Smart Headwear

-
• Developing a truly cancelable biometric system remains an unsolved, challenging historical topic as stability and cancelability in biometrics are odds with each other. On one hand, stability requires that biometric traits are immutable and hard to change; on the other hand, cancelability requires that biometric traits are erasable and easy to change.
• We argued that the most secure cryptographic credentials can be obtained by ERP brainwave signals. Based on this idea, we investigated a new cancelable psycho-physiological approach for secure and trustworthy user authentication on mobile platforms (e.g., smart VR headwears). With the scalp-recorded ERP neurofeedback, new ERP credentials can be generated via different stimuli sets even if the ERP template database is breached.
-
• Developing a truly cancelable biometric system remains an unsolved, challenging historical topic as stability and cancelability in biometrics are odds with each other. On one hand, stability requires that biometric traits are immutable and hard to change; on the other hand, cancelability requires that biometric traits are erasable and easy to change.
Sustainable Cyber-Physical Ecosystem: Operations, Complaince, and Accountability
-
† Cross-layer Architecture for Energy-efficient 3D Printing
-
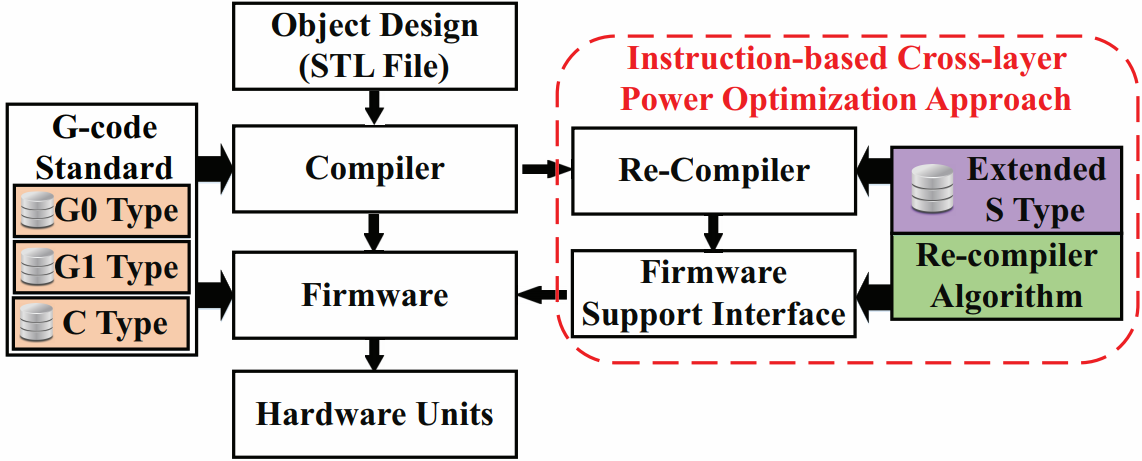
• 3D printing progresses towards versatile fields with portable battery-powered 3D printers working on a limited energy budget. Meanwhile, the global energy demand keeps increasing. According to the report by International Energy Outlook (IEO) in 2016, the manufacturing industry consumes about 54% of the world’s total delivered energy. While reducing the energy use in manufacturing is a core problem in industrial sustainability and national economics, it will be critical to optimize the energy consumption of 3D printing for the new ear of manufacturing.
• The proposed cross-layer solution, 3DGates, spans the instruction set, the firmware and the compiler to dramatically reduce the energy consumption of the 3D printing process. This study is the first research to understand the energy behavior of the typical 3D printing instructions. It is an immediately deployable solution that can be applied on commercially off-the-shelf 3D printers without inducing any hardware alteration or quality defects.
-
• 3D printing progresses towards versatile fields with portable battery-powered 3D printers working on a limited energy budget. Meanwhile, the global energy demand keeps increasing. According to the report by International Energy Outlook (IEO) in 2016, the manufacturing industry consumes about 54% of the world’s total delivered energy. While reducing the energy use in manufacturing is a core problem in industrial sustainability and national economics, it will be critical to optimize the energy consumption of 3D printing for the new ear of manufacturing.
-
† Smartphone-based Side Channel Monitoring for Compliant 3D Printing

-
• 3D printing has been increasingly applied to fabricate highly intellectual property (IP) sensitive products in automotive, aerospace, retail and biomedicine. However, the related IP protection issues in 3D printers are still largely unexplored. This work disclosed such a vulnerability and exhibited that the printing process can be reconstructed based on the smartphone side-channel information.
• With such a technique, we can further enable the ethical 3D printing by ensuring the compliant printing process through real-time monitoring.
-
• 3D printing has been increasingly applied to fabricate highly intellectual property (IP) sensitive products in automotive, aerospace, retail and biomedicine. However, the related IP protection issues in 3D printers are still largely unexplored. This work disclosed such a vulnerability and exhibited that the printing process can be reconstructed based on the smartphone side-channel information.
-
† Unclonable QR Code via 3D Printing
-
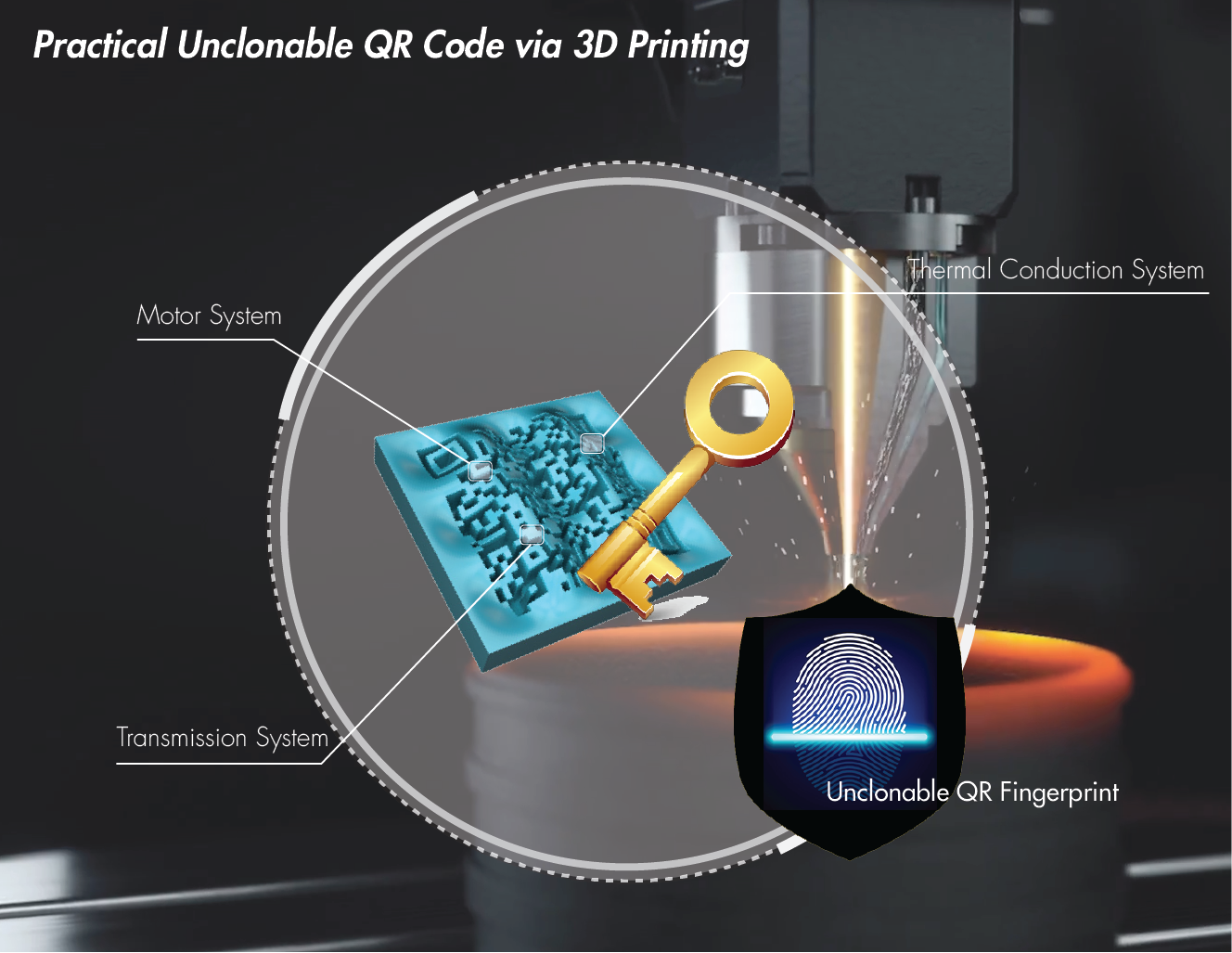
• 3D printing market keeps growing. However, the conventional anti-counterfeit tagging technologies (e.g., 1D barcode, watermark and radio-frequency identification) are not effective because: (1) they are prone to security attacks once the attacker hacks the anti-counterfeit protocol; (2) they require extra hardware and specific external devices to process the identity.
• Considering the popluarity of the Quick Response (QR) code, we envision the novel 3D prints authentication scheme where the user can just use a smartphone to scan the embedded QR code. This work raises the concept of integrating the product design with its QR code. It can immediately enhance product security because the 3D printed QR code is not detachable from the product.
-
• 3D printing market keeps growing. However, the conventional anti-counterfeit tagging technologies (e.g., 1D barcode, watermark and radio-frequency identification) are not effective because: (1) they are prone to security attacks once the attacker hacks the anti-counterfeit protocol; (2) they require extra hardware and specific external devices to process the identity.
Mobile Health
-
† Stroke Rehabilitation
-
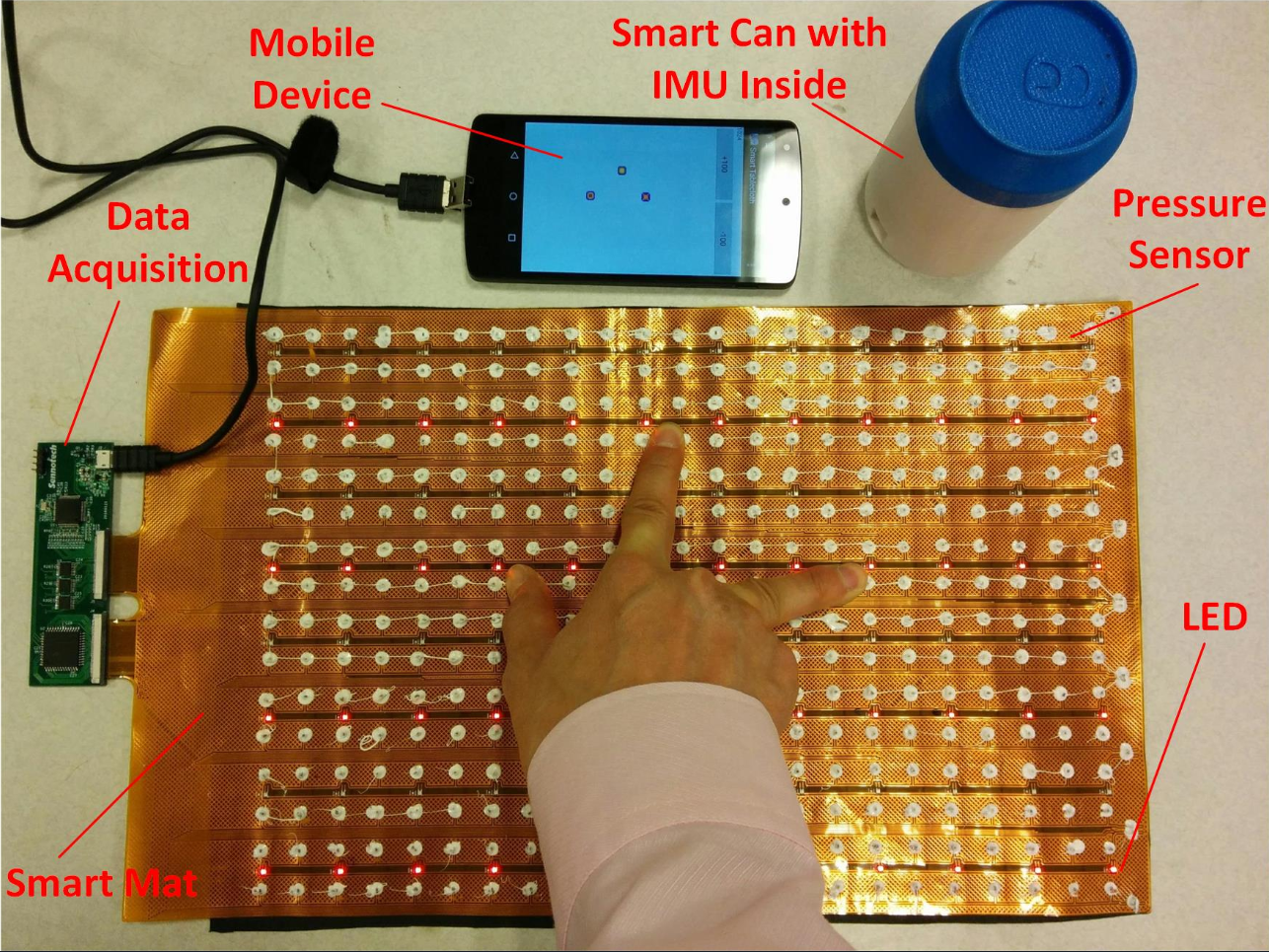
• Formal rehabilitation is well organized in the acute stages of stroke, there is minimal professional support of rehabilitation across the lifespan.
• We introduced an upper extremity rehabilitation system, QM-FOrMS, by integrating cost-effective portable sensors and clinically verified motion quality analysis towards individuals with upper limb motor deficits.
• The system provides a set of unilateral and bilateral functional activities that the patient can select and work on refining their quality of movement.
-
• Formal rehabilitation is well organized in the acute stages of stroke, there is minimal professional support of rehabilitation across the lifespan.
-
† Autism Spectrum Disorders (ASD) Timely Screening
-
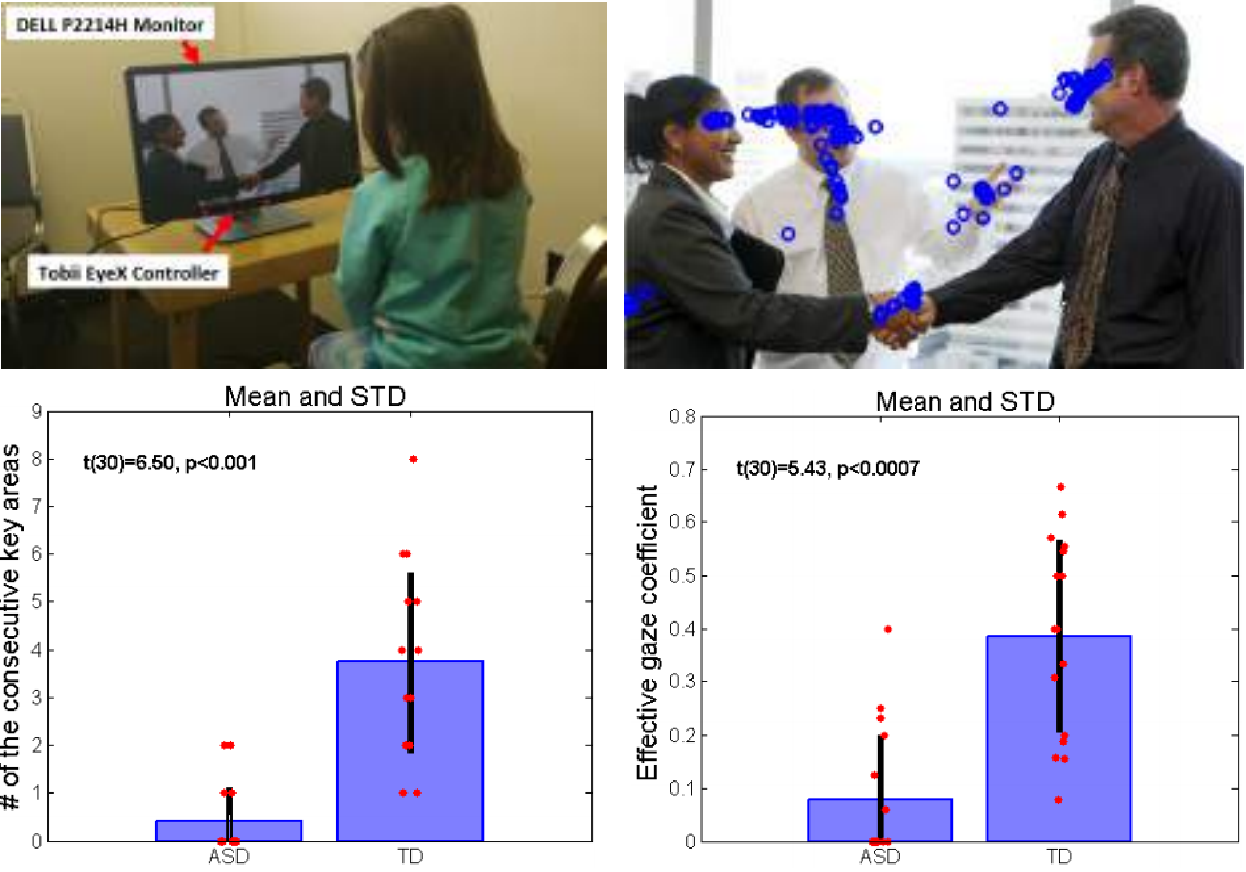
• Autism spectrum disorder (ASD) is a complex developmental disability characterized by deficits in social interaction. 1.5% of children (one out 68 children) in the United States are diagnosed with autism as of 2014. The current screening for autism highly depends on the subjective judgment of parents and primary medical doctors.
• Studies have shown that children with ASD have different social parsing strategies and respond atypically when compared to same-aged peers with typical development. Among the multiple biofeedbacks, we explored gaze behavior because it reveals the parsing strategy the participant uses to achieve social content.
• We found limitation in the existing fixation-pattern-based ASD gaze works that they cannot indicate how the brain actually combines all the visual information it receives and processes the visual scene it is observing. We studied the dynamic connection information within the gaze pattern of the ASD patients to explore how they lacks the ability to understand the relationship between the key objects within the social scene.
-
• Autism spectrum disorder (ASD) is a complex developmental disability characterized by deficits in social interaction. 1.5% of children (one out 68 children) in the United States are diagnosed with autism as of 2014. The current screening for autism highly depends on the subjective judgment of parents and primary medical doctors.
-
† Noncontact Sleep Monitoring System for Sleep Disorder
-
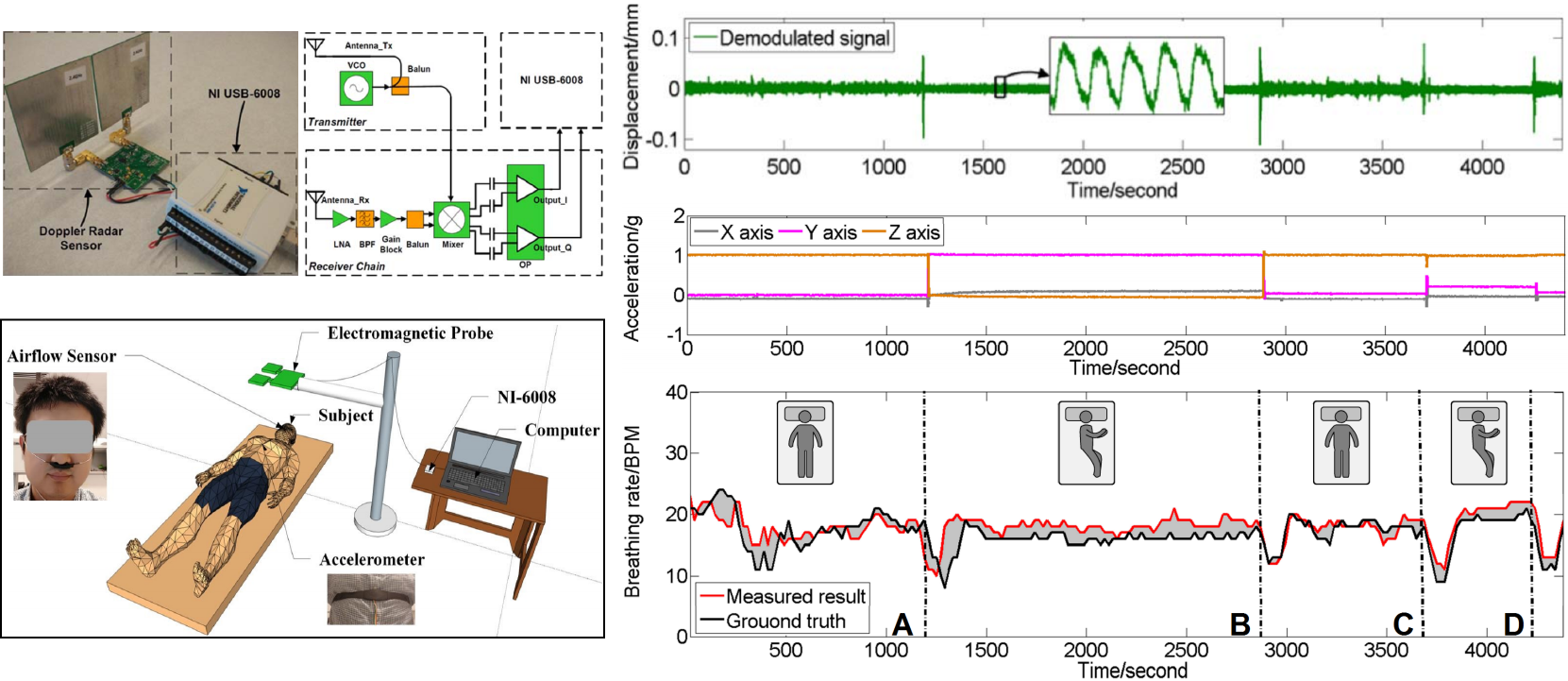
• There is a growing recognition of the adverse effects from poor sleep quality and sleep disorders, including obesity, diabetes, and hypertension.
• We developed a noncontact sleep monitoring system using a COTS-based Doppler radar sensor, which can capture the movement and breathing signal precisely.
• We designed a new sleep status recognition framework, which performs the signal segmentation, time-domain and frequent-domain features extraction, and sleep status detection, including on-bed movement, bed exit, and breathing section.
-
• There is a growing recognition of the adverse effects from poor sleep quality and sleep disorders, including obesity, diabetes, and hypertension.
-
† Wearable Acoustic Sensor System for Food Intake Recognition
-
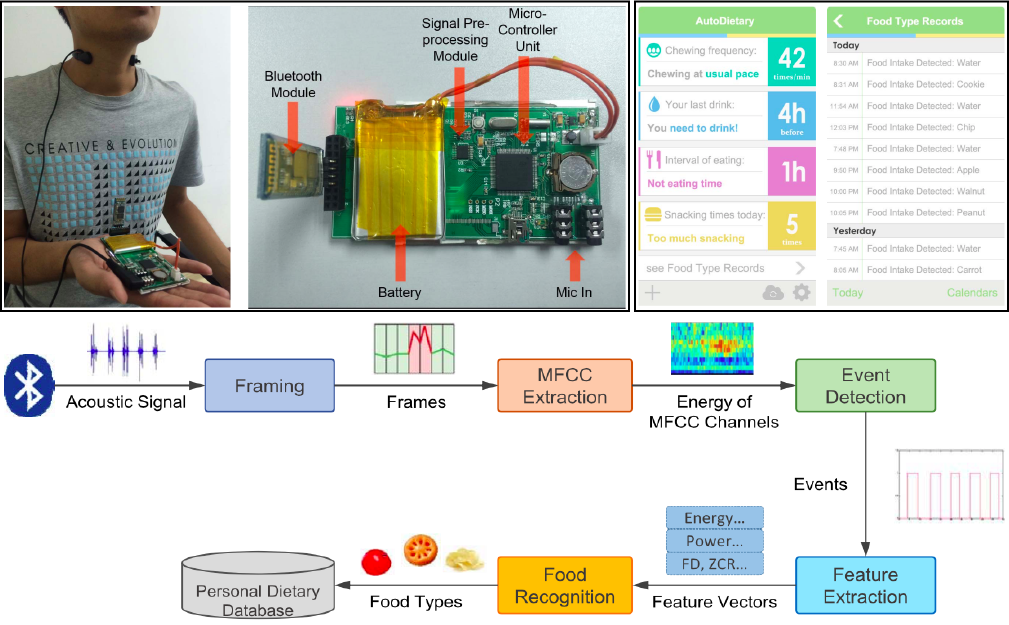
• We built AutoDietary, a necklae-like wearable system to recognize food types by monitoring eating process. The system is composed of Embedded Hardware System and Smartphone Application.
• The hardware platform integrated with acoustic sensors was developed to pick up high-quality sound signals of eating behaviors in a convenient and non-invasive manner.
• The bluetooth-based smartphone application not only aggregates food recognition results but also provides the information in a user-friendly way and offers suggestions on healthier eating.
-
• We built AutoDietary, a necklae-like wearable system to recognize food types by monitoring eating process. The system is composed of Embedded Hardware System and Smartphone Application.